Bluetooth Low Energy Solutions (BLE)
Next-generation RTLS, Custom BLE Gateways and Beacons
Why C3-Wireless For BLE?
As experts in Wi-Fi mission-critical networks, C3-Wireless provided RF Fingerprinting site surveys and implemented many Wi-Fi Real-Time Location Services (RTLS) systems based on Wi-Fi, when that was the leading option. We understand the real “gotchas” and limitations of RTLS platforms beyond the marketing promises. When Bluetooth Low Energy (BLE) was first introduced, C3-Wireless immediately recognized it as a disruptive technology for RTLS solutions due to its clear advantages of low-cost hardware and long battery life.
We immediately looked for enterprise-class BLE gateways, and when we could not find a suitable solution, we set forth developing our own BLE Gateways and beacons. Today, we have sold tens of thousands of BLE Gateways and hundreds of thousands of beacons. Our technology is unsurpassed in performance and capability. Our Gateways have the most advanced on-board intelligence, allowing them to process more than 500 unique beacons per second. And we can custom build unique BLE firmware and hardware in form factors that meet whatever use-case our customers can envision. Our enterprise-class management platform allows for managing thousands of Gateways per venue.
C3-Wireless knows how to implement mission-critical technology. We leverage our experience and expertise into building platforms and hardware that works, allow our software development partners to focus on building front-end solutions that meet their customer’s needs without having to worry about making the back-end work.
In 2020, after years of learning what works and does not work well for BLE RTLS we are excited to introduce a game-changing invention called SmartRelay. This new platform offers what no other BLE platform has been able to deliver before: Sub-room level accuracy without using triangulation, with updates in seconds at a lower hardware and implementation cost than any other BLE or non-BLE RTLS solution available today.
SmartRelay RTLS Platform
Sub-room level (bed/bay/chair) accuracy. Updates in seconds. Proximity only, no triangulation required. Low-cost hardware and batteries. Implement in hours\days, not weeks with no special skillsets required.
Anyone that has compared today’s RTLS technologies knows that BLE has nearly every advantage over RFID, Wi-Fi, UWB, IR, UltraSound, etc. except one. Accuracy. BLE’s low power is not well-suited to use with triangulation, which at best is difficult to design for and implement correctly. And until SmartRelay, using proximity would get you zone level accuracy or up to room level if you added a BLE gateway to every room.
Download a comparison of different RTLS technologies below.
DownloadOur patent pending SmartRelay BLE technology is a game-changer because customer’s can now get sub-room level accuracy (bed/bay/chair) using simple proximity while only requiring a minimal number of BLE gateways.
For an in-depth technical brief on how SmartRelay works, download the information below.
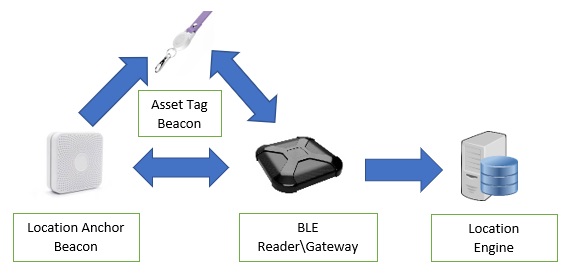
DownloadAt a high level, the SmartRelay platform consists of three main hardware components. A BLE Gateway, a Location Anchor (a static iBeacon or Secure Beacon geo-referenced in a location engine) and an asset tag (worn by a person or placed on a thing) running SmartRelay firmware.
Traditional BLE Gateways (ours included) are geo-referenced to a location engine and use RSSI to calculate the distance between a BLE beacon (iBeacon or otherwise) and the Gateway to estimate in proximity where the beacon is located somewhere within the Gateway’s cell. Our Gateways use advanced intelligence to provide the best calculations and options for filtering, etc. available. Our BLE Gateways can also process proprietary BLE sensor beacons, where calculating distance is not needed.
While the SmartRelay platform does require BLE Gateways to transmit data to a location engine or analytics platform, just like with BLE sensor beacons, it does not take into account the distance between an asset tag beacon and the Gateway. Instead, the asset tag determines the closest Location Anchor (stationary iBeacon) and reports this information to the location engine through the BLE Gateway. The BLE Gateway only needs to hear the BLE advertisement coming from the asset tag.
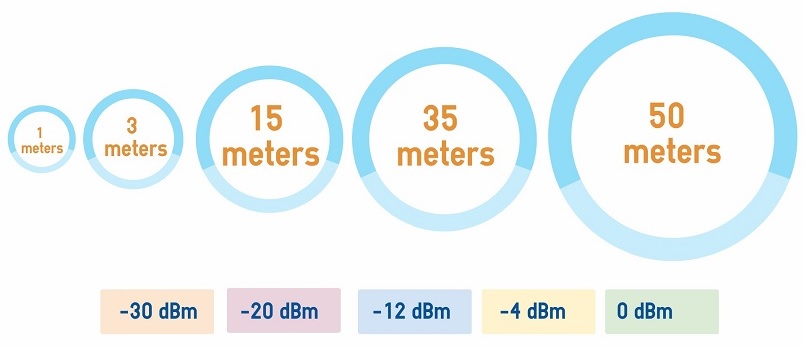
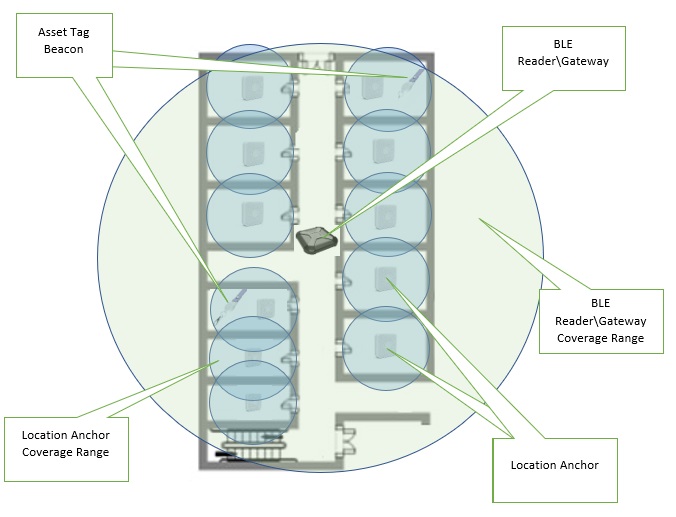
Location Anchors are stationary iBeacons (or stationary Secure iBeacons) that are physically placed in a room or part of a room (e.g bed/bay/chair) and then geo-referenced in the location engine (e.g. Location Anchor 1 is in Room 103, Bed 2). A location anchor can have a large cell (zone) that can, for example, cover an entire office area, or can have a small cell (microzone) covering a part of a room. Each area is sometimes known as a Point of Interest (PoI) and a venue can have as many PoIs as desired.
Location Anchors are low cost, can run for years on batteries, and can be installed in minutes without any special skillset or tools. Just determine how many PoIs are desired and add one Location Anchor per PoI. The more PoIs, the more accurate the system.
SmartRelay Location Anchors work like BLE beacons do in a Wayfinding App. In fact, The SmartRelay platform can also use beacons already deployed for Wayfinding. Asset tags running SmartRelay firmware act similar to a smartphone identifying its location based on its proximity to a BLE beacon.
The SmartRelay firmware is similar to iBeacon or EddyStone or other proprietary BLE firmware in that it can run on just about any beacon hardware that conforms to the BLE standard. Note: While SmartRelay can run on nearly any BLE beacon hardware, depending on use case, some beacons may not be appropriate for use in the SmartRelay platform. In general, use beacons CR2032 batteries or larger.
The asset tag determines which Location Anchor is the closest and transmits that information in a standard BLE advertisement packet through the BLE Gateway to the location engine. No complicated triangulation is required. No special hardware is required. And because the asset tag performs the location calculation, the work is distributed so the solution scales without requiring massive computing resources on-premises to accurately determine location.
All information can be sent to the C3-Wireless Location Engine or directly to a partner or customer’s own location engine. If using the C3-Wireless Location Engine, it can be installed as a cloud instance or on-premises. An open API system is provided to make integration into front-end applications easy.
SmartRelay RTLS platforms are less expensive and easier to install than competing systems, offer sub-room level accuracy and can update in seconds to track people and things, and backend location engine logic is simple to integrate into front-end platforms.
C3-Wireless Bluetooth Low Energy Gateways
Far beyond doing basic BLE GATT reads, our enterprise-class BLE Gateways are the most powerful solution available, capable of reading 500+ unique beacons per second.
Our BLE Gateways feature user-configurable pre-processing to filter out non-interesting packets and make decisions on what data to transmit and how often. They read any BLE 4x and 5x standard packet and can easily be updated to process proprietary data packets from BLE sensor beacons, security beacons, etc.
C3-Wireless BLE Gateways push data simultaneously to one or many local or cloud-based platforms. Customers have the option of implementing a C3-Wireless location engine platform with open APIs, or receive the data directly into their own system or systems. Customers and partners are not required to be tied to C3-Wireless back-end systems, protecting third parties from vendor lock or security concerns.
Use our enterprise-class management platform to manage dozens to thousands of BLE Gateways.
Key Features and Benefits:
| Feature | Benefit |
|---|---|
| Supports any 4.x or 5.x standard BLE packet | Any iBeacon, Eddystone, or proprietary BLE beacons are accepted and v5 support allows for future proofing. |
| Reads hundreds of beacons per second (550+ tested) | Makes high-density solutions possible and allows for beacons to advertise more frequently leading to greater accuracy. |
| External antenna connector | Allows for ideal antenna placement and type depending on use case. External antennas typically also capture more accurate reads. |
| Proprietary, advanced processing algorithms | Dramatically improves network bandwidth utilization and quality of reads which improves location detection accuracy and provides greater control over configurations for various use cases. |
| 802.3af standard Power over Ethernet | Only one low-power network cable required, allowing for easier implementation and ideal device placement. Low power requirement means less expensive PoE switches needed. |
| Local or cloud-based management platform | System can run 100% independently from outside end user’s organization. Allows centralized management for group configuration and firmware updates. |
| DHCP Option 43 and 60 support | Allows for fast and easy provisioning. |
| Supports advertising virtual BLE beacons | Allows for additional use-cases such as wayfinding. |
| Features push topology to aggregator or directly to third-party platform using a lightweight network protocol | Simplifies application development and provides greater flexibility while minimizing network traffic. |
Cisco-Certified Third-Party Module
C3-Wireless is proud to have partnered with DeCurtis Corporation to develop the first ever Cisco-Certified Third-Party module for the Cisco 3800 Series access points, the DeCurtis DC-BR3800-01 BLE Module, powered by C3-Wireless.
The DC-BR3800-01 BLE Module is a BLE 5.x Device that can advertise beacons as well as read more than 550 simultaneous beacons per second. The proprietary, advanced processing algorithms dramatically improve network bandwidth utilization and quality of reads, which provides greater location detection accuracy and control over configurations for various use cases. It gets power and network connectivity through the access point, but otherwise operates completely independently.
Features and Benefits:
| Feature | Benefit |
|---|---|
| Supports any 4.x or 5.x standard BLE packet | Any iBeacon, Eddystone, or proprietary BLE beacons are accepted and v5 support allows for future proofing. |
| Reads hundreds of beacons per second | Makes high-density solutions possible and allows for beacons to advertise more frequently leading to greater accuracy |
| External antenna connector | Allows for ideal antenna placement and type depending on use case. External antennas typically also capture more accurate reads. |
| Proprietary, advanced processing algorithms | Dramatically improves network bandwidth utilization and quality of reads which improves location detection accuracy and provides greater control over configurations for various use cases. |
| Side loading module | Reduces installation time and costs. No need to run new power or network cables. No need to remove access point to install. |
| Local or cloud-based management platform | System can run 100% independently from outside end user’s organization. Allows centralized management for group configuration and firmware updates. |
| DHCP Option 43 and 60 support Peak power <2W | Allows for fast and easy provisioning. Low impact on access point, ensuring access point has enough resources to operate radios and advanced features. |
| Certified by Cisco, FCC, ETSI and for safety | Ensures device will not void Cisco warranties and can be used in North America or Europe. |
Datasheet
More information can be found here:
Deployment Guide
The DC-BR3800-01 Deployment Guide can be found here:
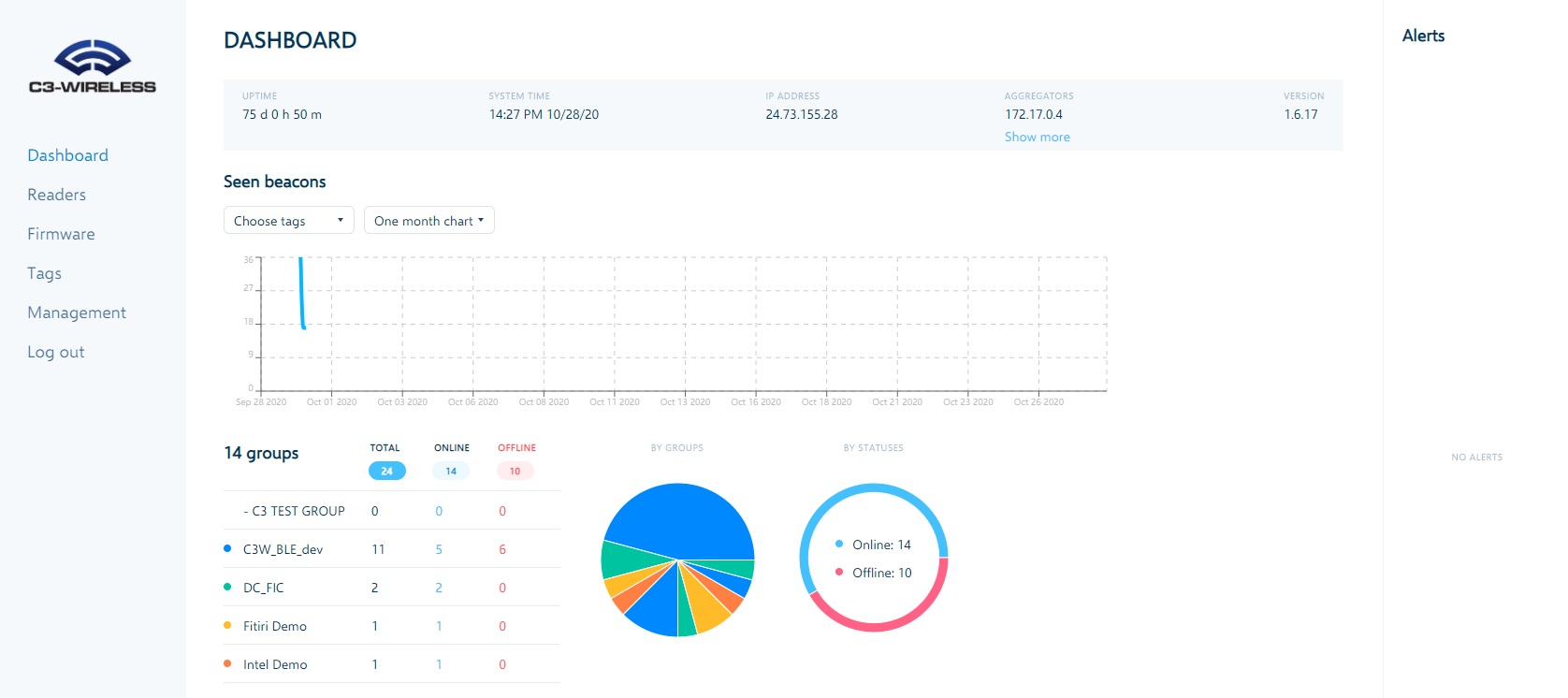
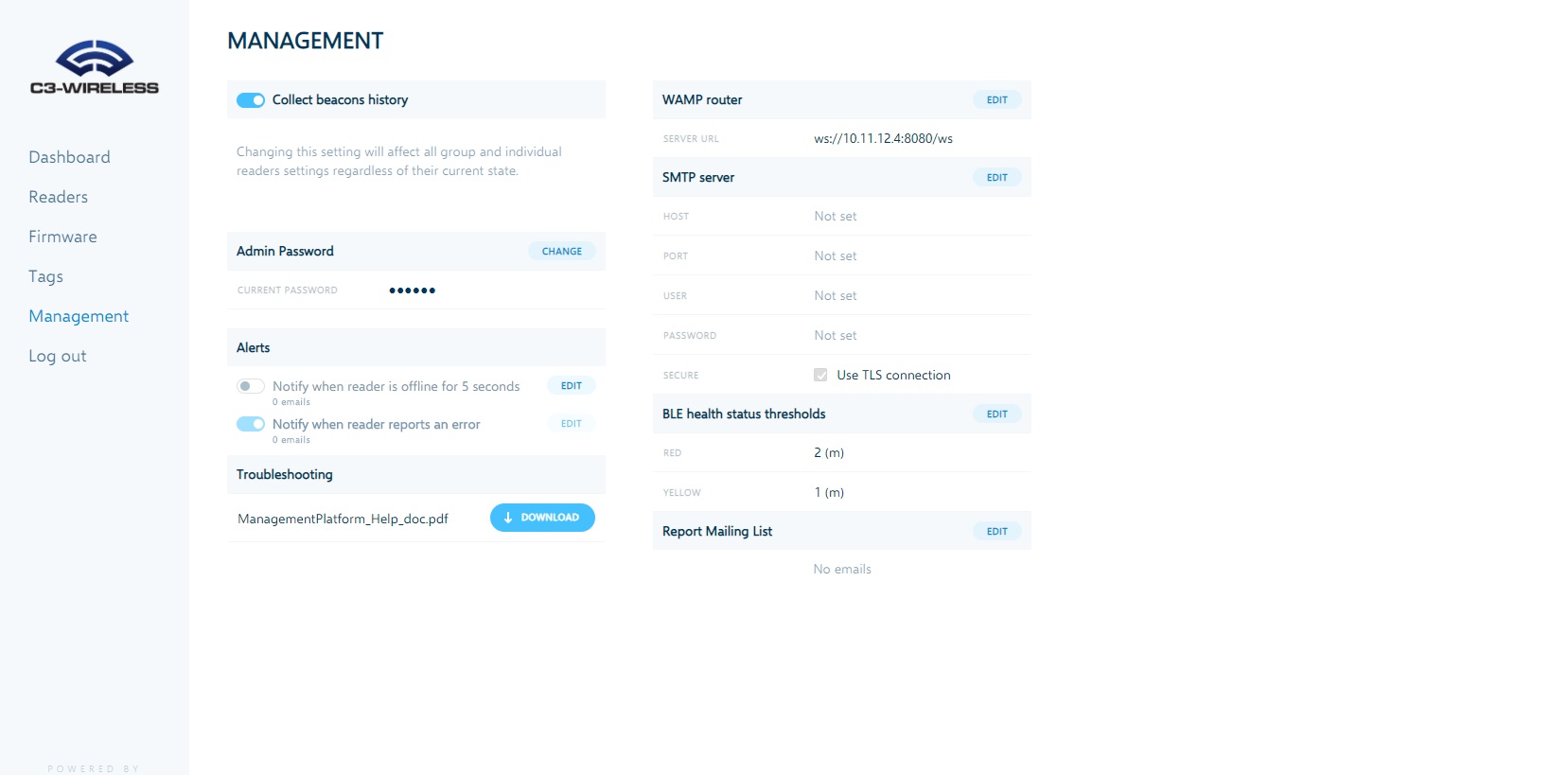
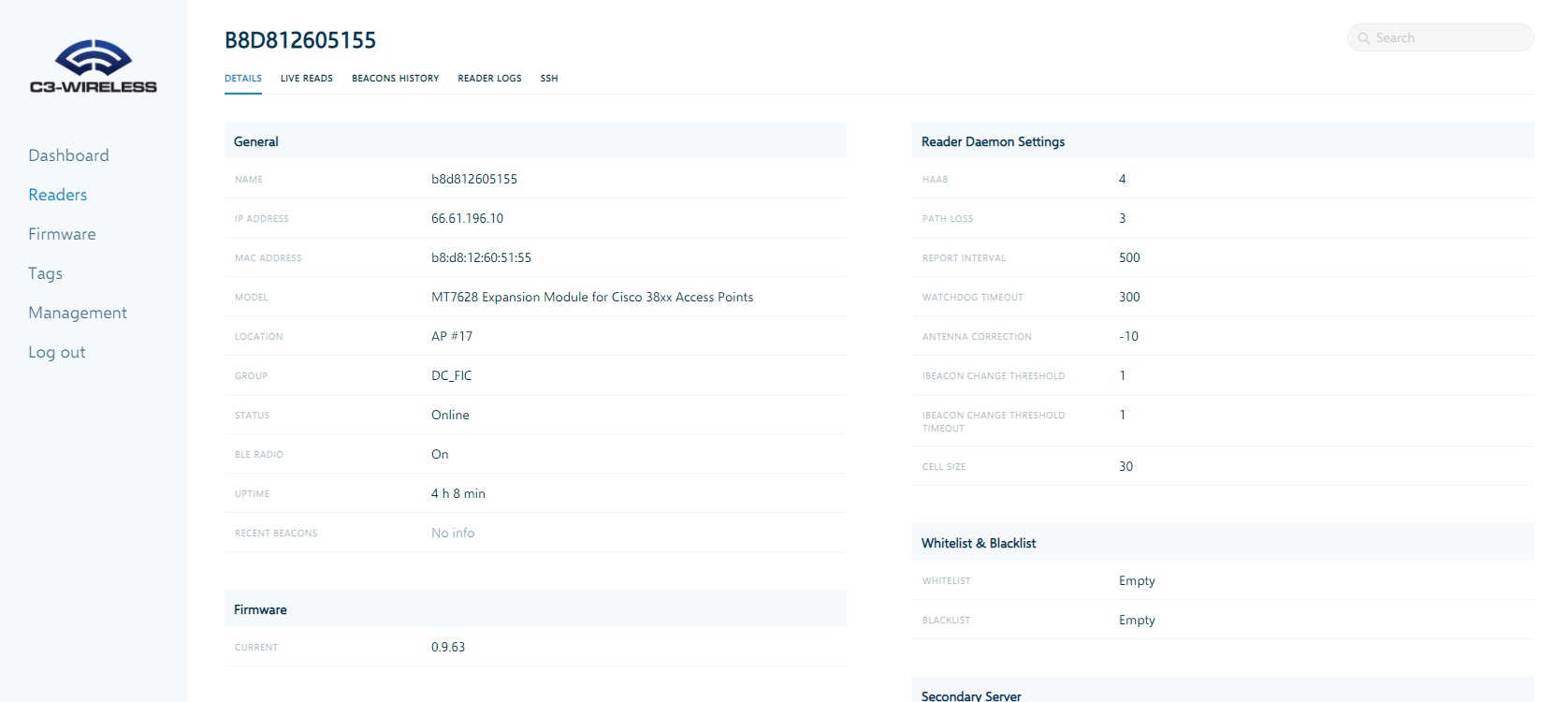
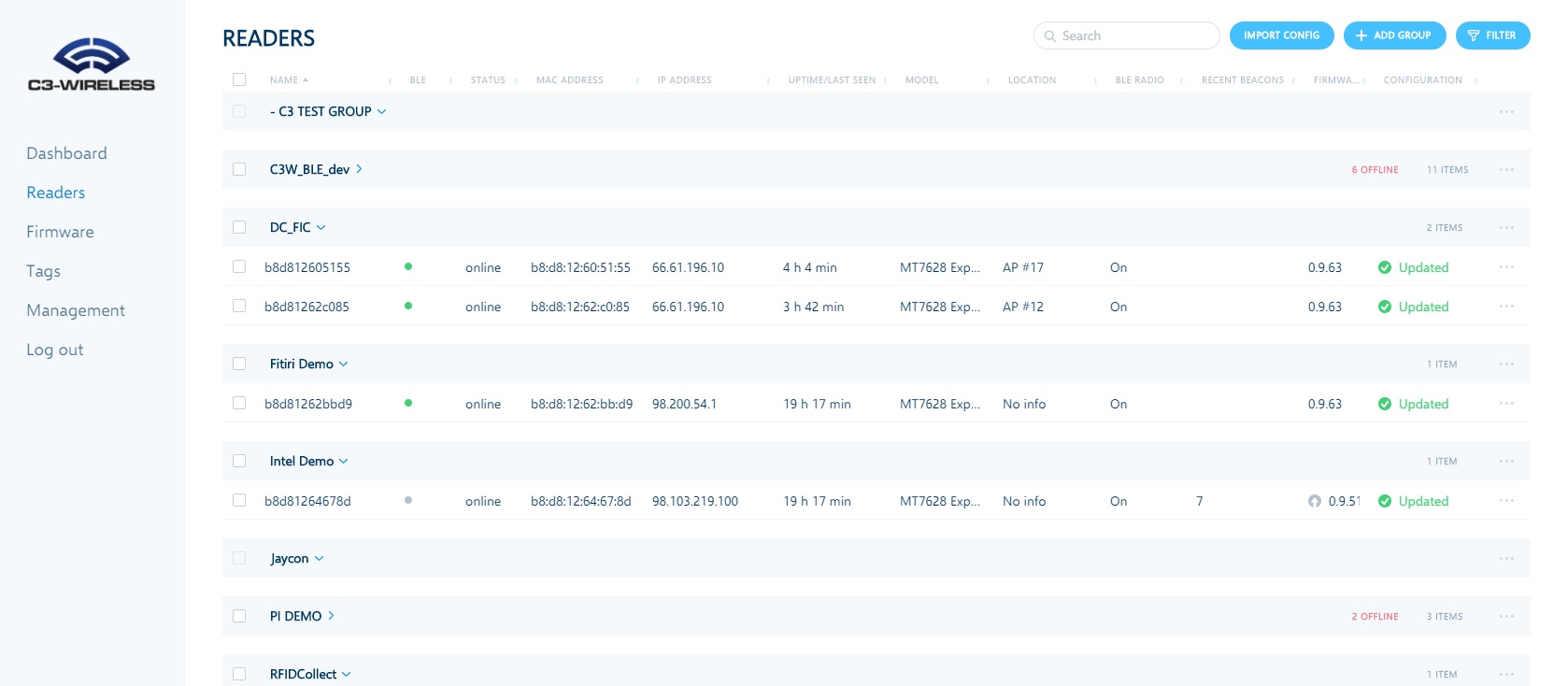
C3-Wireless Management Platform
C3-Wireless BLE Readers “push” data to an end-point. This end-point is typically a C3-Wireless aggregator that makes it easy to create connectors for integration into third-party applications while also connecting to the C3-Wireless BLE Reader management platform. The aggregator and management platform can be local to the network or cloud-based.
Note: The BLE Readers can also send data directly to third-party developers, completely independent of C3-Wireless.
Our management platform makes it easy to centrally manage onboarding, configuration and updates for larger implementations by groups or individually. The platform helps administrators troubleshoot implementations by providing views to historic data, live reads and alerts.
Click the images to view fullscreen.

Bluetooth
Low Energy Beacons
C3-Wireless has worked with third-party vendor beacons in the last few years. What we have discovered is most do not live up to their advertised capabilities. So we decided to build our own enterprise-class beacons made with high-quality parts and customizable firmware.
Because we manufacture our own devices, we can create custom form factors or proprietary firmware solutions. Examples of past projects include adding battery life measurement to iBeacons, slowing down advertisement rates for longer battery life, or completely proprietary solutions for frictionless access control.
Our standard beacon features a “smart slot” that allows the beacon to be powered using either a large CR2450 battery for multi-year usage, or an alternate power source from USB, wire tap or even solar power.
We provide an IP65 capable enclosure for outdoor installations and harsh environments such as cement plants.
Our keychain beacons are used for tracking people or for providing frictionless access control (see this case study) and feature a small form factor with replaceable battery and push button control.
Users have complete control over power levels and advertisement rates, and if using iBeacon or hybrid firmware, UUID, Major and Minor settings.
Frictionless Access Control
Using Bluetooth Low Energy
Anyone that has a new car with the ability to sense when the key fob is nearby to automatically unlock the door, understands the convenience of “frictionless” access control.
Frictionless basically means not having to pull a key out of your pocket or swipe a badge across a scanner.
Using C3-Wireless BLE Readers and a key-chain BLE beacon or other BLE wearable running our proprietary code, that same frictionless access control is now available for smart homes or offices.
Our BLE access control protocol is connectionless, and beacons act like wireless one-time password generators (similar to Yubikey). Though authentication information is transmitted in the clear, the authentication server verifies that the sender possesses the correct beacon key and that the message is unchanged. The probability of guessing the correct authentication tag is less than 1 in 4.2 billion.
Attackers cannot generate valid beacon packets or replay valid packets they intercepted. If an attacker obtains a beacon they can use that beacon until it is deactivated (similar to obtaining a key card). However they are not able to generate valid packets for any other beacons since all beacon keys are unique.
Cloning a beacon is possible but significantly difficult and is detectable by the system. Once beacons are deactivated, they are useless. Attackers can create new unique beacon IDs and secret keys, but because the matching data isn’t in the authentication database, the beacon is useless as well.
For more information about Frictionless Access Control, download the whitepaper here or contact C3-Wireless.
Case Study #1
DeCurtis Corporation and C3-Wireless Bring BLE Readers to the Cisco 3800 Series Access Point
DeCurtis Corporation is the first choice for proximity-based guest experience solutions, custom application development and strategy enhancement for restaurants, cruise lines, theme parks and the hospitality industry.
C3-Wireless and DeCurtis Corporation combined their BLE expertise to create the first-ever third-party module for the Cisco 3800 Series Access Point, the DC-BR3800-01 BLE 5x Module. This module physically plugs into the Cisco 3800 series access point’s expansion module for power and network uplink, and provides the ability to transmit or read any BLE 4x or 5x standard advertisement. It passed rigorous Cisco Certification testing to make it the most advanced BLE solution available today.
The platform is built for large-scale, enterprise-class deployments and integrates with management platforms, location aggregators and the DeCurtis Experience Platform to provide unrivaled guest experiences.

Case Study #2
Sigga and C3-Wireless Team up for Preventative Maintenance
Sigga is a global provider of SAP certified mobile enterprise applications. Sigga Brizzo is a complete mobile maintenance and inspection solution for SAP PM.
Sigga identified BLE as a great technology to improve equipment identification and validate a user was at the location of inspection when the inspection was completed. By placing a beacon at an inspection location, the application automatically identifies the piece of equipment from within the mobile app. If the user is not within a pre-defined proximity of the equipment, they are not able to unlock the item to be inspected until they come within range.
Sigga needed a beacon that could operate in harsh industrial environments such as concrete plants and be configurable and adjustable to set proper boundaries from location to location. They selected C3-Wireless beacons because they met all their requirements at an attractive price point. C3-Wireless professional services teams helped implement the solution.
![]()
Case Study #3
Digital Interiors and C3-Wireless Partner for Frictionless Access Control
Digital Interiors has specialized in designing, installing and servicing smart technology solutions for home and businesses to the highest standards for more than 20 years.
When a new luxury condominium complex was proposed in Midtown Atlanta, Digital Interiors was tasked with providing a technology solution to offer the highest level of customer experience possible. Leveraging their extensive experience in smart building automation, they worked with C3-Wireless to design a custom-built frictionless access control solution using C3-Wireless BLE Readers and beacons.
Similar to new cars that unlock when you touch the door handle if the key fob is within range, residents simply walk up to a door to automatically unlock it using a keychain beacon with specialized, highly-secure BLE access control firmware.
A beacon placed in a car automatically opens the property’s outdoor lift gates, outdoor garage doors, and individual garage door. Pressing a button on the key fob closes the garage door while exterior doors using proximity to unlock or automatically call down elevators.
C3-Wireless built the highly-secure, frictionless, and connectionless access control protocol to work over BLE. For more information about BLE Frictional Access Control, download the whitepaper below:
Download Whitepaper
![]()
Case Study #4
L&T Chooses C3-Wireless Platform for Automated Loss Tracking
L&T Technology Services is a leading global Engineering Research and Design Company offering services and solutions to all major industries including Transportation, Industrial Products, Telecom & Hi-Tech, Medical Devices and Process Industry.
Working with a large brewery, L&T helped them identify a way to improve how they tracked product loss during the packaging process by moving from a manual to an automated processes. This would allow them to get better accuracy and insight into where losses occurred. By better addressing these losses, the brewery could save millions of dollars per year.
L&T originally planned to track the processes using Active RFID. However, after reviewing the advantages of BLE over Active RFID, especially comparing the cost of each solution’s reader, L&T decided to use BLE instead. L&T partnered with C3-Wireless to provide the hardware, including readers and beacons, and develop the custom application.
One reason for using C3-Wireless beacons was the ability for them to work in harsh conditions where they would be exposed to liquids. The IP65 beacon enclosures provided the needed protection.
![]()